Synopsis: With the development of renewable energy sources, a significant amount of distributed generation based on renewable energy sources (RES) has been added within the distribution network. The model of a modern energy system is based on a network architecture of interconnected generation, storage or load elements, whose basic feature is a highly distributed location within the distribution systems.Due to the interactions that have a final impact on the stable operation of the distribution network, the implementation of metering and control of system elements in a centralised or area correlated manner is required. Therefore, there is a need to organise communication to distributed facilities in a secure manner taking into account the specific technological requirements. The article describes an outline of issues related to secure communication with distributed energy facilities in the context of requirements related, among others, to IEC 61850 standardisation.
INTRODUCTION
The process of change that has been underway for many years within the electricity generation, shifting the share of generation to geographically dispersed renewable sources, has had a profound effect on issues relating to modelling, design, but also supervision and maintenance of the electricity system. The extent of these changes mainly affects the electricity distribution infrastructure, but not without impact on the transmission infrastructure. Maintaining the capacity to transmit the generated energy with the requirements of stability of the power grid and providing electricity with guaranteed parameters to the consumer requires immediate transformation of the solutions and information systems used. By transformation, we can mean here changes both in solutions within substation automation, methods and protocols, but also evolution in systems responsible for communication with distributed power devices in order to correlate them with the entire system.
Solutions based on a set of standards and documents described as IEC 61850, where fully digital measurement, protection and control methods are defined and interconnected through a communication network based mainly on Ethernet solutions, play an increasingly important role in modern digital power systems. Ethernet communication is, however, subject to certain rigours here due to technological requirements for protocols performing measurement and protection functions, such as guaranteed maximum delay or the ability to carry precise time synchronisation. Thus, when considering situations where an identical communication architecture emerges along with a distributed and fragmented architecture of power equipment, the challenges of maintaining traffic integrity and potentially associated security risks should be noted. Area-centralised communication is needed to maintain system stability, and its absence or disruption in a worst-case data intrusion resulting from a cyber-attack could contribute to system failure and collapse. The situation is made more difficult by the need to take into account technological requirements that make it difficult to apply security mechanisms known from IT network solutions. This publication will consider the general requirements and recommendations for Distributed Energy Resources (DER) communication systems that need to be considered when designing a system to create a working and secure architecture.
COMMUNICATION SYSTEM ARCHITECTURE AND TRANSMISSION REQUIREMENTS ASSOCIATED WITH THE TECHNOLOGIES USED
When considering the energy system model with DER resources shown in Figure 1, a picture emerges of energy islands associated with the location of smaller sources of conventional generation, RES generation as well as correlated storage elements that are attached to the distribution system. Generation and storage elements can be grouped into clusters and, as part of natural processes, a group of devices may need to operate autonomously. However, all distributed resources operate within the distribution network infrastructure together with the necessary metering, protection and control elements. Each system element in a network of automatic digital power solutions is an element that has an internal controller with communication functions. The behaviour of a generation or storage element can therefore be programmed and controlled locally and/or remotely.
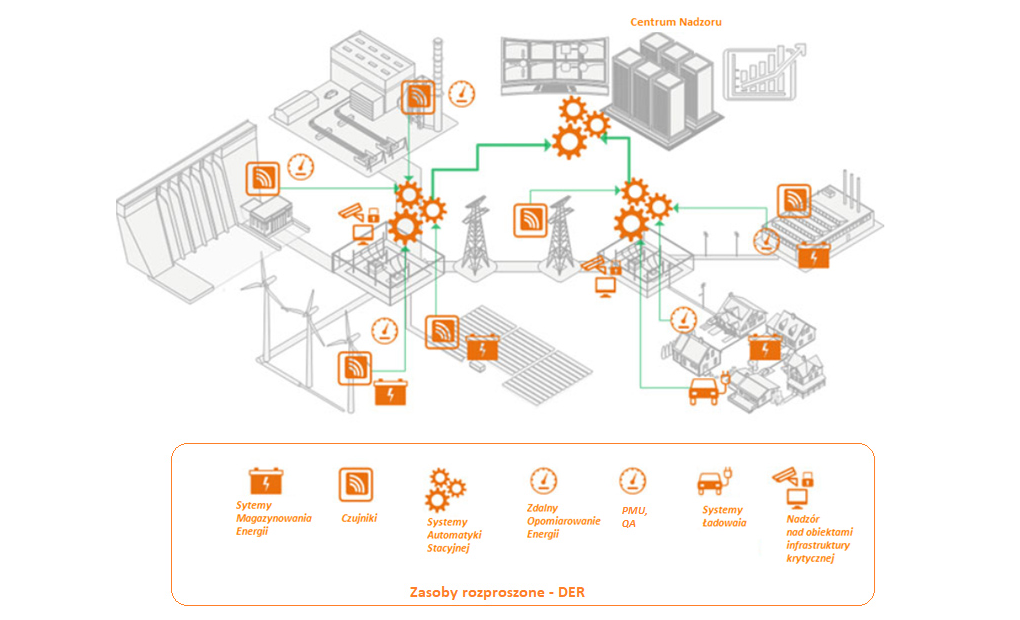
Figure 1: Example architecture for communicating with distributed resources
The concept of controllability can and must be driven by the need to keep the system in a stable state to deliver electricity to consumers with the required quality indicators. While at present smaller generation and storage systems operate autonomously controlling parameters locally, it is already clear that this approach will give rise to a number of problems. There is competition for the ability to feed energy into the system, as well as competition between economic factors that destabilise the system and technical factors that require set parameters. There is therefore only one solution, namely the control and coordination of resources in a centralised manner by the distribution network operator (DSO). To achieve this, it is therefore necessary to organise continuous and secure communication with the DERs, but also with the metering and protection devices.
The evolution of digital automated substation solutions based on IEC 61850 documents has introduced new metering as well as protection technologies such as Sampled Values (SV), Phasor Measurement Units (PMU) or Generic Object Oriented Substation Events (GOOSE) to substations. These are essential for managing and maintaining a dynamic distribution system. However, they define for us new requirements on the data transmission network, i.e. maximum delay, packet jitter and the quality of the time synchronisation we need to deliver to the measurement and protection devices. Thus, an important aspect for a correctly designed and built distributed communication network is to understand the critical role of meeting the aforementioned network parameters on the correct functioning of the technology. The next step will be to implement adequate security solutions in such a way as not to disrupt the functioning of the mentioned solutions.
An important issue becomes the selection of solutions to be used within the station and the internal technological network for communication with host systems, as well as those that must be used outside the station and delivered to DER resources.
Figure 2 shows an example of a communication model with the associated requirements for network parameters highlighted.

Fig. 2. Example communication model with breakdown of areas within the system
The ranges of the technologies mentioned and the required latency depending on the protocols used are presented. The required accuracy of precise time synchronisation, the distribution of which is now centralised, is also defined. It is important to note that IEC 61850 defines the operation of certain solutions within Layer 2 of the model, which is an additional complication for taking communications beyond the station using Wide Area Network (WAN) mechanisms. According to the standards and as shown in the figure, the maximum latency values for certain security functions for the communication path should not exceed 3ms. In contrast, the accuracy of precise time synchronisation for measuring devices should be within 1us. When we superimpose security functions in the form of encryption, access control, tracking, we face an implementation challenge. The question arises as to what encryption mechanisms and communication channels should be used. Also, what should the path switching for protection look like, especially since IEC 61850 recommends the use of PRP/HSR lossless protection protocol technology in security functions. The answers to the aforementioned questions will be presented in Chapter 4 after a consideration of the security standards operating within the infrastructure and energy solutions and threat models.
SECURITY STANDARDISATION, RECOMMENDATIONS AND RISKS
As part of the work on security issues in energy communication infrastructures, two standards, actually two sets of documents have been developed under collective names, viz:
1. IEC TS 62443 - Security for industrial process measurement and control - Network and system Security
2. IEC TS 62351 - Power system management and associated information exchange - Data and Communication Security
IEC TS 62433, focuses on communication and control security for industrial systems. This standard aims to provide guidelines and recommendations for securing these systems against cyber threats. It provides information on how to identify and assess threats, design safeguards, monitor systems and respond to cybersecurity incidents in the context of communication systems in industrial applications. Within the standard, security levels from SL1 to SL4 have been defined, the fulfilment of which determines the level of resilience of a system. Although the standard is not dedicated strictly to energy applications, it is often used for security specifications in energy infrastructures due to its just collection of requirements and mature form.
IEC TS 62351, on the other hand, is a group of standards for security in control and management systems in the power industry. The collection of documents treats security issues very broadly. This includes data integrity protection, confidentiality and authentication, threat models and many other aspects. Nevertheless, the documents are under constant editing and development and, according to the author, the definition of final requirements for some parts is still a long way off. However, it is in this group of documents that an attempt to formulate a guide for communication security in power grids in the context of technology requirements appears.
Turning to the consideration of security issues in the energy communication system, the following should be mentioned as the main tasks to achieve the goal of increasing the level of security.
- Authentication: All devices should be verified before they are connected to the energy network or before they start communicating with them. - Authentication helps to prevent the connection of unauthorised DER resources.
- Authorisation: Once a device has been authenticated, the system should determine what activities and functions are available to the DER based on its authorisations. This prevents unauthorised access and control of the device.
- Data encryption: Data transmitted between the energy management system and DER assets should be encrypted to ensure data confidentiality and integrity. Encryption improves data protection against unauthorised access and data manipulation.
- Traffic splitting: Splitting traffic across multiple links can make it significantly more difficult to implement an eavesdropping or takedown attack.
- Protection against cyber-attacks: Digital assets are susceptible to cyber-attacks, which can lead to power disruptions or loss of control. Management systems must therefore be equipped with mechanisms to protect against attacks, such as firewalls, exposure detection and software updates.
- Key management: the management of cryptographic keys is important for the security of communication with DER resources. Keys should be stored and managed securely to avoid potential security breaches.
- Monitoring and response: Energy management systems should be able to monitor communications with DER resources in real time and detect anomalies. Responding to potential threats is key to maintaining network security. An important aspect especially for MITM (Man in the Middle) attacks is to constantly monitor links and devices for breaches.
- Protecting physical access: Protecting physical access to facilities and devices and infrastructure is a key aspect in preventing the most dangerous integrity breaches. They are the ones that can result in the most dangerous effects of attacks.
- Standardisation and regulation: The organisation should have defined internal regulations for the security of communications with DER resources. Compliance with these regulations is key to ensuring compliance and security.
When considering the range of threats and typical models, we can divide them into groups such as:
- Unauthorised access to information: This involves eavesdropping on the physical transmission medium, analysing traffic, scanning radio links, or accessing physical documents containing network architecture, IP addresses, keys or passwords.
- Unauthorised access and modification of information: This involves gaining physical access to the medium or control at a level that allows not only eavesdropping but also modification of information. This can be achieved by physically plugging in third-party devices carrying out an MITM attack into the infrastructure, as well as by modifying routing configurations in such a way as to allow full filtering and modification of traffic. This is a particularly dangerous scenario in the context of energy systems.
- Denial of service or prevention of authorised access: This consists in modifying the behaviour of a network element in such a way (virus, Trojan, spoofing, jamming, others) that it causes the improper performance of dedicated tasks (e.g. security, synchronisation or other critical tasks) or the impossibility of communicating in order to obtain information or reconfigure devices.
It is, of course, possible to isolate yet other threat models. Nevertheless, these seem particularly important from the level of system impact within the communication area.
PROPOSED SOLUTIONS FOR ACCESS TO DISTRIBUTED POWER EQUIPMENT ON THE BASIS OF BITSTREAM S.A.'S OFFER.
Taking into account the above-mentioned considerations of technological requirements as well as security aspects, BITSTREAM S.A. has developed solutions enabling the implementation of secure communication with DER resources while maintaining the services and parameters required by IEC 61850. The development of the solutions took into account the need to transfer precise time synchronisation according to the profiles required by the standard and an accuracy of <1us, as well as traffic issues related to GOOSE security functions and the requirements for contributed delays.
Due to the need to maintain the operability of the solution in different parts of the network, a software solution for routing with security functions was developed, which can be embedded in an external hardware platform using its resources, as well as in dedicated BITSTREAM device solutions allowing for layer-2 encryption, transfer of precise PTP v.2 (Precision Time Protocol v.2) time synchronisation according to the required profiles, and additional monitoring functions. An example of the system architecture is shown in Figure 3.
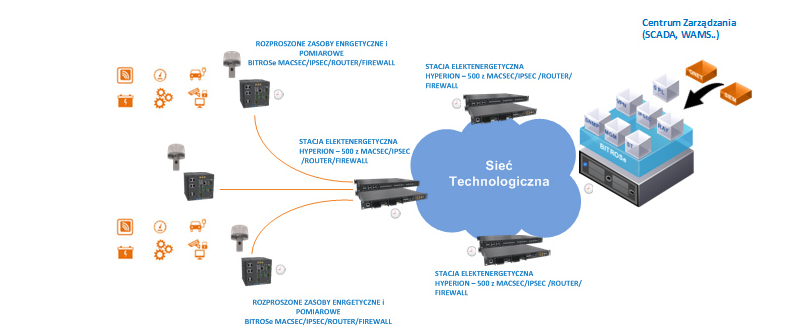
Fig. 3. BITSTREAM solutions for communication with distributed resources
The integrated BITROSe security platform allows, among other things, the implementation of the following security mechanisms:
- Monitoring and protection of breaches in the physical layer and physical part of the device to protect against MITM attacks from the physical infrastructure and to detect breaches.
- L2 layer encryption (MACSEC) for time-critical services and L3 (IPSEC, VPN).
- Possibility to combine cryptographic systems [CS2], e.g. MACSEC - >IPSEC, IPSEC -> IPSEC, etc.
- Dynamic routing systems with L3 (ISO OSI) network convergence below 20ms and typical mechanisms like OSFP, BGP, others.
- Dividing traffic into links with prioritisation.
- L3 network separation (Virtual Routers) and L2 independent MACSEC channels.
- Configuration and management security, access (AAA) Authentication, Authorisation and Accounting, disabling access, services, configuration via card memory.
- Firewall L2,L3,L4 with (DNAT) Destination Network Address Translation.
- Lossless protection for data switching - 0 packet loss L3 and optionally L2 technologies.
- Built-in interfaces to 4G or 5G LTE radio systems as backup or primary communication channels in the event that physical links are not available.
- Compliance with IEC TS 62443 - Security for industrial process measurement and control - Network and system Security.
- Support for IEC 61850 digital automated substation protocols, (MMS, GOOSE, PDC).
- Additional interfaces (serial communication, contact, measurement) for data integration with RES.
- Precise synchronisation of PTP, GNSS time for measuring devices (Quality Analysers, PMU, others).
- Possibility of direct cooperation with SCADA.
The L2 MACSEC encryption mechanisms used make it possible to securely implement precise time synchronisation services, the transmission of GOOSE security signals or the use of PMU security functions. For less time-sensitive protocols, encryption techniques at higher layers can be freely combined. Integrity protection covers tampering events in the physical layer as well as in the device itself.
By separating the software part from the hardware part, the whole thing can be implemented in a variety of hardware configurations from the more advanced to the simple, giving free cost scaling depending on the implementation site.
In summary, by relying on standard encryption mechanisms and a range of additional functions unique to the BITSTREAM solution, it is possible to achieve secure and operational communication solutions for IEC 61850 technology, which are essential for RES power generation. The premise of the digital solutions is to use control supported by machine learning algorithms allowing semi-automatic or fully automatic control of resources in the system under designated quality indicators. This assumption requires communication with each element of the infrastructure and, for reliability, it must be implemented in a secure manner.
Krzysztof Nowacki, M.Sc.
Research and Development Director Bitstream S.A
LITERATURE
1. IEC TS 612351-1 Power systems management and associated information exchange – Data and communications security. Part 1: Communication network and system security – Introduction to security issues
2. IEC TS 62433-1 Industrial communication networks – Network and system security – Part 3-1: Security technologies for industrial automation and control systems
3. IEC 62439-3 (International Standard). Industrial Communication Networks – High Availability Automation Networks – Part 3: Parallel Redundancy Protocol (PRP) and High-availability Seamless Redundancy (HSR)
4. IEEE Std C37.238™-2017, IEEE Standard Profile for Use of IEEE 1588™ Precision Time Protocol in Power System Applications
5. IEC TR 61850-90-12 :2020 Communication networks and systems for power utility automation – Part 90-12: Wide area network engineering guidelines
6. IEEE 1588-2019 – IEEE Standard for a Precision Clock Synchronization Protocol for Networked Measurement and Control Systems
7. IEC TR 61850-90-5:2012 Communication networks and systems for power utility automation – Part 90-5: Use of IEC 61850 to transmit synchrophasor information according to IEEE C37.118
8. Practical aspects of IEC 61850-9-2 implementation in microprocessor-based protection and control IEDs
9. WP-IEC-61850-Architectures – 2021
10. IEC 61850-5:2013 – Communication requirements for functions and device models










